DNS Data Exfiltration
DNS Data Exfiltration Leverages DNS Tunneling
DNS Data Exfiltration is one of the uses of DNS Tunneling. Although there are many DNS Tunneling implementations, they all rely on the ability of clients to perform DNS queries. DNS Tunneling software allows users to do:
- Relatively innocuous things, such as getting free airport Wi-Fi
- Potentially dangerous acts, such as using SSH over DNS to evade corporate firewalls
- Outright malicious activities, such as stealing sensitive information and malware finding command and control points
In the case of the last, clients evade detection by breaking data down into query-sized chunks, disguising sensitive data as DNS queries, and sending them to malicious DNS servers on the far end who can unpack these queries and reconstruct the data.
How DNS Data Exfiltration Works
DNS Data Exfiltration is like stealing someone’s car without opening the garage door: You have to break the car down into small chunks that fit through the doors and windows, and then rebuild the car outside. Except in the case of data exfiltration, the malware breaks down files, sometimes even encrypting each chunk, before sneaking them off your premises to reassemble.
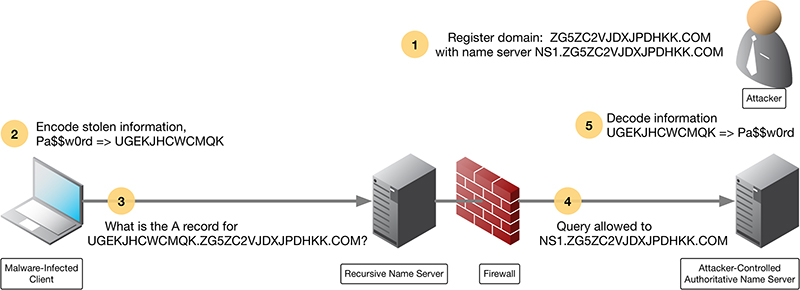
Figure 2-5 illustrates a simplified flow of how data exfiltration works over DNS:
- The attacker registers the domain name ZG5ZC2VJDXJPDHKK.COM, and sets up name server NS1.ZG5ZC2VJDXJPDHKK.COM
- The infected client encodes stolen information, in this case, the text “Pa$$w0rd”, into “UGEKJHCWCMQK”
- The client makes the DNS query for the domain with the encoded password as a subdomain: UGEKJHCWCMQK.ZG5ZC2VJDXJPDHKK.COM
- A recursive name server finds the authoritative name server NS1.ZG5ZC2VJDXJPDHKK.COM and sends the query there.
- The attacker recognizes the subdomain value as the encoded password. The attacker decodes the information UGEKJHCWCMQK back to recover “Pa$$w0rd”
In this example, it is not necessary for the client to receive a response from the malicious server, because the goal was to send information out. However, the process can easily include the malicious server sending back an exploit to be executed on the infected client.
How to Detect DNS Data Exfiltration
Because the attacker controls both ends of the conversation, they can make the encoding scheme as complex or as simple as they desire. The encoding scheme can evolve over time to evade detection: So, even if you learned to recognize one pattern today, it may be a different pattern tomorrow. One way to stop simpler DNS Data Exfiltration is to block the malicious domain altogether through technologies such as Response Policy Zones (RPZ).
However, recognizing this possibility, attackers can register multiple domain names to use in rotation to evade detection; so, simply blocking one bad domain (ZG5ZC2VJDXJPDHKK.COM in the example) is not going to be effective in stopping this attack. In fact, this latter approach is so commonly used, many attackers employ a Domain Generation Algorithm (DGA) to automatically generate random domain names and register them, several hundreds and thousands at a time.
These queries are very difficult to recognize, even to trained professionals. To recognize a DNS Data Exfiltration in progress requires a complex process of lexical analysis, which is difficult given the high volume and frequency of DNS queries. By the time a human analyst reaches a conclusion, the attackers have already stolen what they came for and moved on. This is a job ill-suited for humans but ideal for machines. Through superior computing power and machine-learning, a computer system can detect DNS Data Exfiltration not only faster but with more accuracy.