DNS and Malware
Just like many other protocols themselves, malware leverages DNS in many ways. From infected hosts identifying command and control points, to DNS Hijacking, to identifying targets in the first phases, malware attempt to exploit the DNS protocol. Malware leverages DNS because it is a trusted protocol used to publish information that is critical to a networking client.
Two specific examples at opposite ends of the Malware and DNS security story are DNS Hijacking and the ransomware, “WannaCry”.
How DNS Hijacking Threatens DNS Security
In DNS Hijacking, malware is used to create DNS Spoofing by changing the clients configured DNS servers, allowing the malicious party to both see what the client is querying and to misdirect the client as desired. This form of DNS Spoofing can dramatically affect the clients behavior and allow reconnaissance of the host and its behavior. A well-known malware variant is DNSChanger, a DNS hijacking trojan. Most often, this trojan is an extremely small file (+/- 1.5 kilobytes) that is designed to change the ‘NameServer’ Registry key value to a custom IP address or link. This called IP address is encrypted in the body of a trojan. As a result of this change, a victim’s device will contact the newly assigned DNS-server to resolve names of different webservers, sometimes randomly. At its peak, DNSChanger was estimated to have infected over four million computers. It was designed to generate revenue through web clicks and referrals, and net the creator Rove Digital, in excess of $14M USD in fraudulent advertising profits. (wikipedia)
While DNS highjacking malware has traditionally been seen on Windows machines, Macintosh computers are now being targeted by malware as well. For example, Mac computers are impacted by the MaMi variant, which sneaks by antivirus software and allows the installation of a new root certificate, from which attackers can choose to do varied nefarious actions.
“WannaCry” Exploits DNS
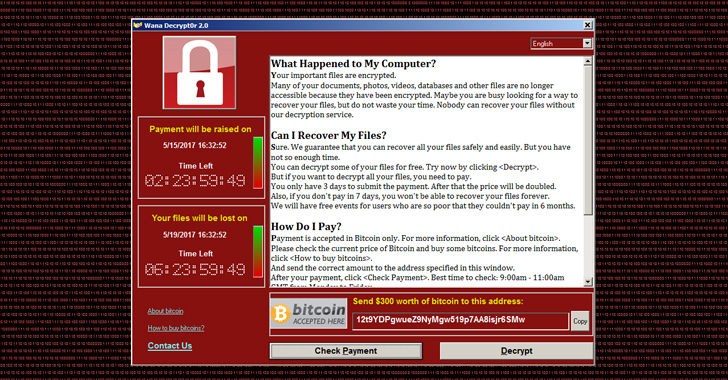
WannaCry ransomware shown in Figure 2-6, launched on May 12, 2017 and impacted hundreds of thousands of computers in 150+ countries. It leveraged a known and patched vulnerability in Microsoft Server Message Block (SMB) to encrypt files on users’ machines and demand ransoms of up to $600 in Bitcoin to return the files. (https://www.infoblox.com/threat-center/) In the example of WannaCry it was actually the kill switch that was tied to DNS. The Ransomware checked if a specific domain name was registered in order to be turned on and off. It actually took the good guys a while to even notice it because DNS is so ever prevalent. But once it was discovered just by registering the domain, they were able to kill the attack.
Figure 2-6: Shows the WannaCry page that was seen once a client was infected.
Another example of malware exploiting DNS as an attack vector is the Mirai malware, which utilized vulnerabilities within Internet of Things (IoT) devices such as IP cameras, printers, baby monitors and home routers. On October 21, 2016,the Mirai malware created a botnet that leveraged a Distributed Denial of Service (DDoS) attack against DNS provider Dyn. The attack, aimed at making money off of Minecraft aficionados and incapacitating rival “minecraft” servers, overwhelmed Dyn, a major DNS service provider. The Mirai malware brought down some of the biggest websites on the internet for much of the east coast of the US and parts of Europe. At its peak, the botnet was leveraging over 1Tb/s of traffic requests, an unprecedented level.
Our final example is malware’s use of DNS infiltration to gain updates and even complete its installation. When a very small malware is downloaded, it often needs to get the rest of its code, updates or even commands on execution. One way it gets this additional data is through DNS infiltration. Much like Data Exfiltration, DNS infiltration relies on the assumption that a client can send DNS queries and receive responses (since every client relies on this behavior.) The client then sends queries to it programmed command and control server and, using the replies to these queries, gathers the information it needs. This information could either be additional malware code or explicit instructions on when and how to act. Because this DNS infiltration relies on DNS queries, and the bad actor controls both the initial malware installation and the DNS server sending responses, these messages can be paced and encrypted as the bad actor chooses.
Bad actors are increasingly using DNS in many facets of malware installation and execution, as the critical role of DNS is increasingly understood. The role of core networking services such as DNS in network security are have become central to network security defense and protection. Advanced, real threat analytics, focused on DNS services, are critical to identifying and preventing potential malware attacks.