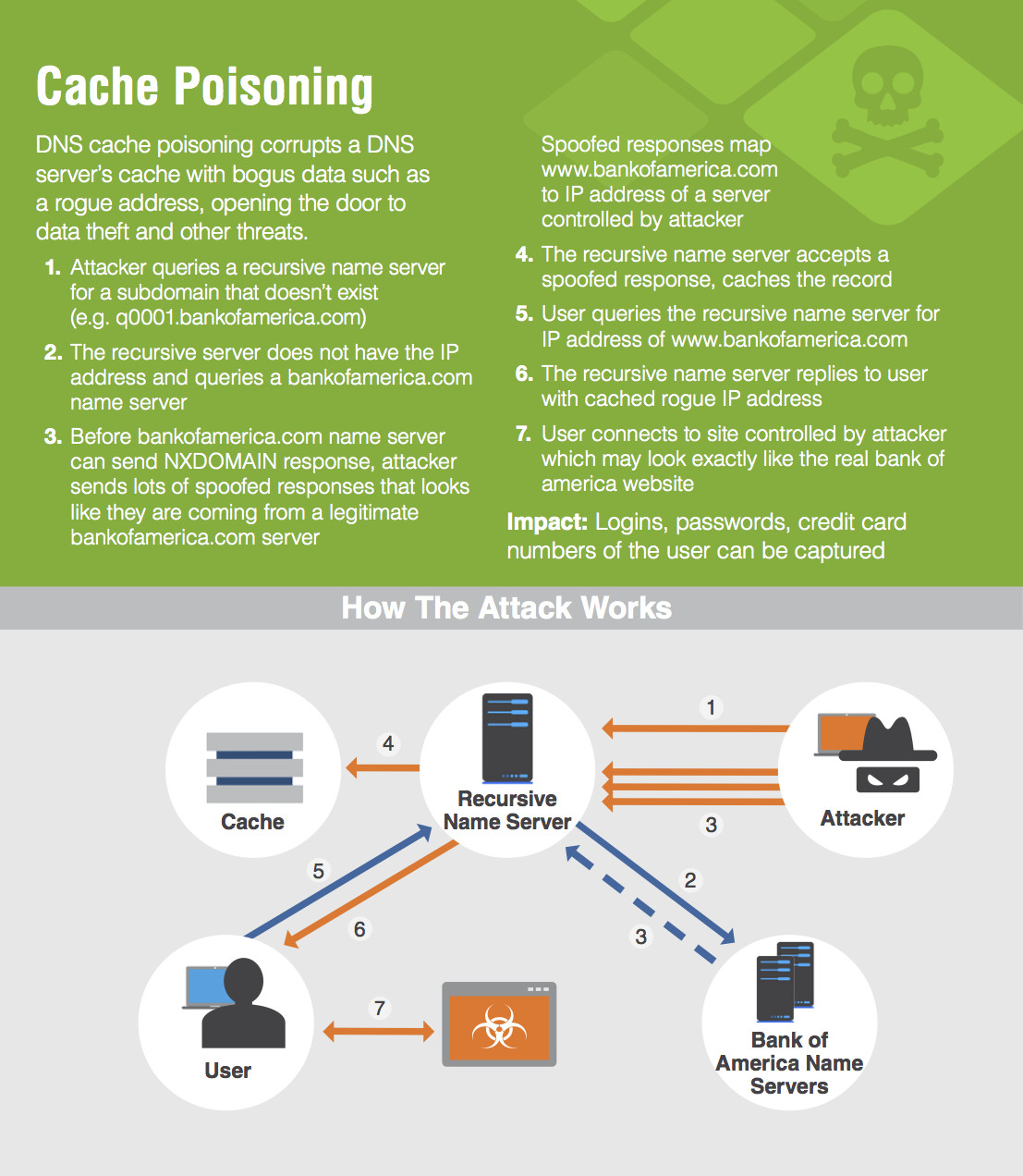
What is a DNS Cache Poisoning?
DNS Cache Poisoning, (aka “DNS Spoofing”), is a cyber attack that exploits vulnerabilities in the domain name system (DNS) by diverting Internet traffic away from legitimate servers and towards fake ones.
DNS cache poisoning enables an attacker to pollute the data in DNS servers—including those managed by your company and your service provider—with bogus information that re-routes your traffic to the attacker’s sites by changing data in DNS to point to their IP address instead of yours. Once traffic is re-routed attacks can take many forms, most of which are extremely difficult to detect:
- An attacker may impersonate your Web presence and collect private data from your customers, partners and employees.
- Your email may be sent to an intermediary server where it is opened and even modified before reaching you or your intended recipient.
- Your anti-spam system can be fooled into allowing malicious email and blocking legitimate email.
- Your Web traffic may be sent to a site that looks like your intended destination (say, your bank’s Web site) but is operated by attackers, where they can collect your user name, accounts and passwords.
- An attacker can use the “Forgot Password” function on your Web site to retrieve your users’ passwords.
- Your Web traffic or ecommerce transactions may be routed through an intermediary site where they are “sniffed” and modified before being passed on to the intended destination.
LEARN MORE ABOUT DNS Cache Poisoning AND RELATED TECHNOLOGIES
- SANS 2023 Survey: Visibility and Attack Surface – White Paper
- Malware Containment and Control — Solution Note
FROM THE INFOBLOX COMMUNITY
ABOUT INFOBLOX
Infoblox unites networking and security to deliver unmatched performance and protection. Trusted by Fortune 100 companies and emerging innovators, we provide real-time visibility and control over who and what connects to your network, so your organization runs faster and stops threats earlier.