What is DNS Tunneling?
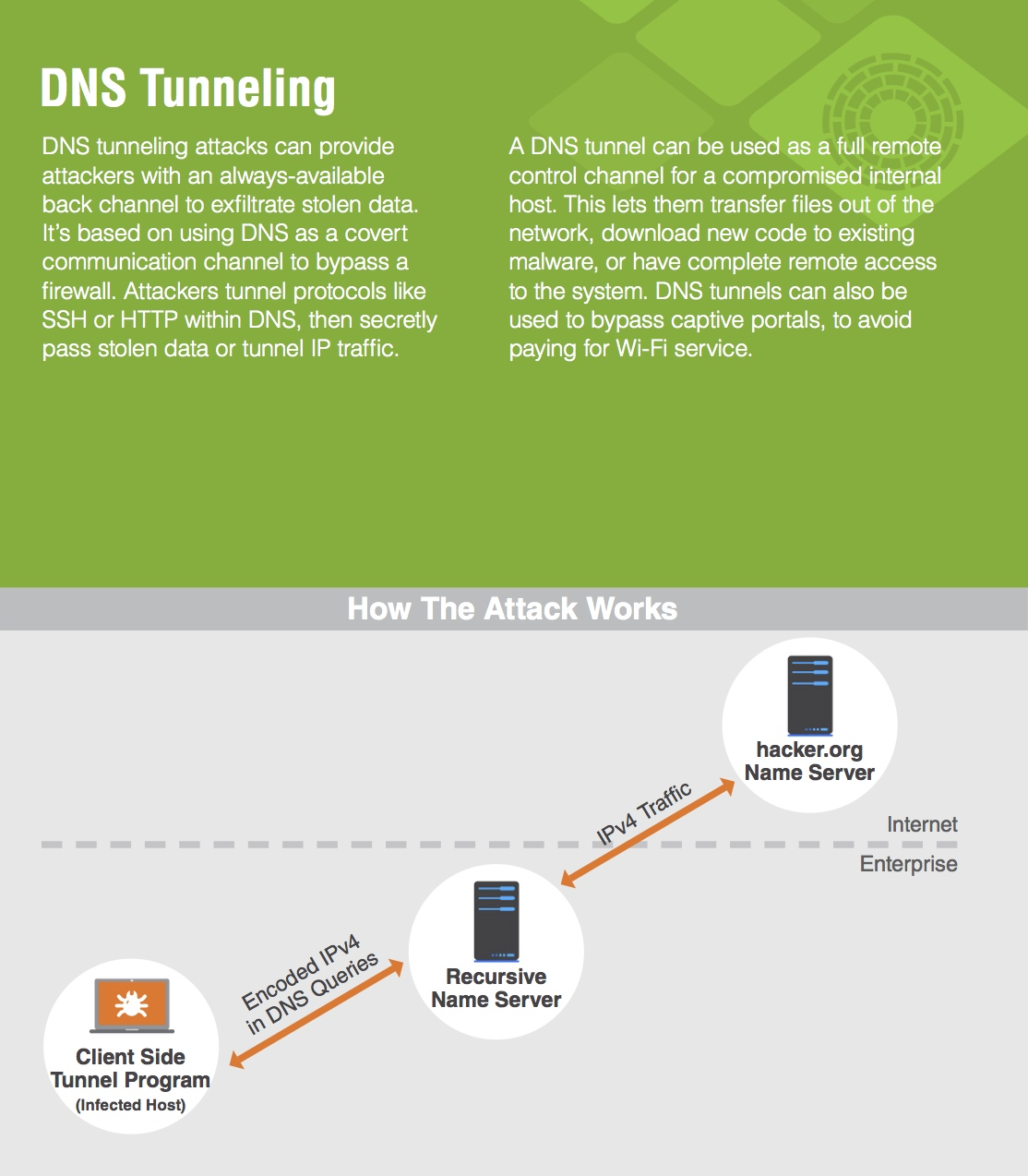
DNS Tunneling is a method of cyber attack that encodes the data of other programs or protocols in DNS queries and responses. DNS tunneling often includes data payloads that can be added to an attacked DNS server and used to control a remote server and applications.
Typically, DNS tunneling requires the compromised system to have external network connectivity, as DNS tunneling requires access to an internal DNS server with network access. Hackers must also control a domain and a server that can act as an authoritative server in order to execute the server-side tunneling and data payload executable programs.
A 2016 Infoblox Security Assessment Report found that 40 percent—nearly half—of files tested by Infoblox show evidence of DNS tunneling. Cybercriminals know that DNS is a well-established and trusted protocol, and have figured out that many organizations do not examine their DNS traffic for malicious activity. DNS tunneling enables these cybercriminals to insert malware or pass stolen information into DNS queries, creating a covert communication channel that bypasses most firewalls. While there are quasi-legitimate uses of DNS tunneling, many instances of tunneling are malicious. There are also several off-the-shelf tunneling toolkits readily available on the Internet, so hackers don’t always need technical sophistication to mount DNS tunneling attacks. At the same time, DNS tunneling is often part of very sophisticated attacks, including those sponsored or directly managed by nation states. For example, the recently uncovered Project Sauron—a particularly advanced threat that is considered likely to have been sponsored by a government—uses DNS tunneling for data exfiltration.
LEARN MORE ABOUT DNS Tunneling AND RELATED TECHNOLOGIES
- SANS 2023 Survey: Visibility and Attack Surface – White Paper
- Infoblox Advanced DNS Protection – Data Sheet
FROM THE INFOBLOX COMMUNITY
ABOUT INFOBLOX
Infoblox unites networking and security to deliver unmatched performance and protection. Trusted by Fortune 100 companies and emerging innovators, we provide real-time visibility and control over who and what connects to your network, so your organization runs faster and stops threats earlier.