What is Protective DNS (PDNS)?
Protective DNS (PDNS) is any security service that analyzes DNS queries and takes action to mitigate threats, leveraging the existing DNS protocol and architecture. Protective DNS prevents access to malware, ransomware, phishing attacks, viruses, malicious sites, and spyware at the source, making the network inherently more secure.
PDNS uses Response Policy Zone (RPZ) functionality, a policy-based DNS resolver that returns answers based on policy criteria. The resolver checks both the domain name queries and the returned IP addresses against threat intelligence, leveraging real-time curated cyber threat insights from various public and private sources to form a list of sites with known malicious content. The DNS resolver then prevents connections to known or suspected malicious sites.
When the PDNS service encounters a malicious or suspicious query, it can respond in several ways. The PDNS may restrict access to the requested domain by returning an NXDOMAIN response, meaning no IP address for the queried domain. The PDNS can also redirect the request to an alternative default page with information that the original domain queried has been blocked. Finally, the PDNS may also “sinkhole” the domain, providing a custom response and preventing or delaying the execution of further cyber threats such as crypto blocking by ransomware or the use of command-and-control protocols. This last approach enables a cybersecurity response team to investigate or initiate infection hunting while a threat remains active.
Protective DNS (PDNS) Services Government Implementation in the UK
The National Cyber Security Centre (NCSC) in the UK created and manages a Protective DNS services solution to protect central government departments and other public sector organizations across the United Kingdom. The PDNS services are currently available at no cost to UK public organizations, including central government, local authorities, devolved administrations, emergency services, NHS organizations, and the Ministry of Defence. The service is one of the NCSC’s widely-deployed Active Cyber Defence capabilities.
Protective DNS (PDNS) Services for Remote Workers
Protective DNS services can provide high network security for remote workers because they can block malicious Internet activity upstream at the source. Remote users can connect to PDNS services using encrypted DNS over HTTPS (DoH) client network protocols, enabling end-users to benefit from end-to-end protection wherever they connect to the Internet.
Protective DNS (PDNS) Domain Classifications
A core capability of PDNS is the ability to categorize domain names based on threat intelligence. PDNS services typically leverage open source, commercial, and governmental information feeds of known malicious domains. These feeds enable coverage of domain names found at numerous points of the network exploitation lifecycle. Some solutions may also detect novel malicious domains based on pattern recognition. The U.S. NSA Cybersecurity & Infrastructure Security Agency (CISA) have outlined the types of domains typically addressed by a PDNS system as follows[i]:
- Phishing: Sites known to host applications that maliciously collect personal or organizational information, including credential harvesting scams. These domains may include close lookalikes of common domains. PDNS can protect users from accidentally connecting to a potentially malicious link.
- Malware distribution and command and control: Sites that are known to serve malicious content or used by threat actors to command-and-control malware. For example, these may include sites hosting malicious JavaScript®2 files or domains that host that collect private information for profiling. PDNS can block and alert on known malicious connection attempts.
- Domain generation algorithms: Sites with programmatically generated domain names that malware uses to circumvent static blocking. Advanced malware – including some botnets – depends on communicating with command and control (C2) infrastructure. Cyber threat actors use domain generation algorithms (DGAs) for malware to circumvent static blocking – either by domain name or IP – through programmatically generating domain names. PDNS offers protection from malware DGAs by analyzing every domain’s textual attributes and tagging those associated with known DGA attributes, such as high entropy.
- Content filtering: Sites whose content is in specific categories against an organization’s access policies. Although an ancillary benefit to malware protection, PDNS can use a categorization of various domains’ use cases (e.g., “gambling”) and warn or block at risk for a given environment.
Protective DNS (PDNS) Core Capabilities
- Block new domains in real-time from the second of registration or creation.
- Enable the delay in the resolution of domains with specific characteristics.
- Control the number of potential domains allowed to attack an organization.
- Collapse and harden all outbound DNS resolution at the time of a malware or ransomware incident.
- Provide real-time and historical visibility into all outbound DNS traffic for incident response and analysis.
Protective DNS (PDNS) Solutions from Infoblox
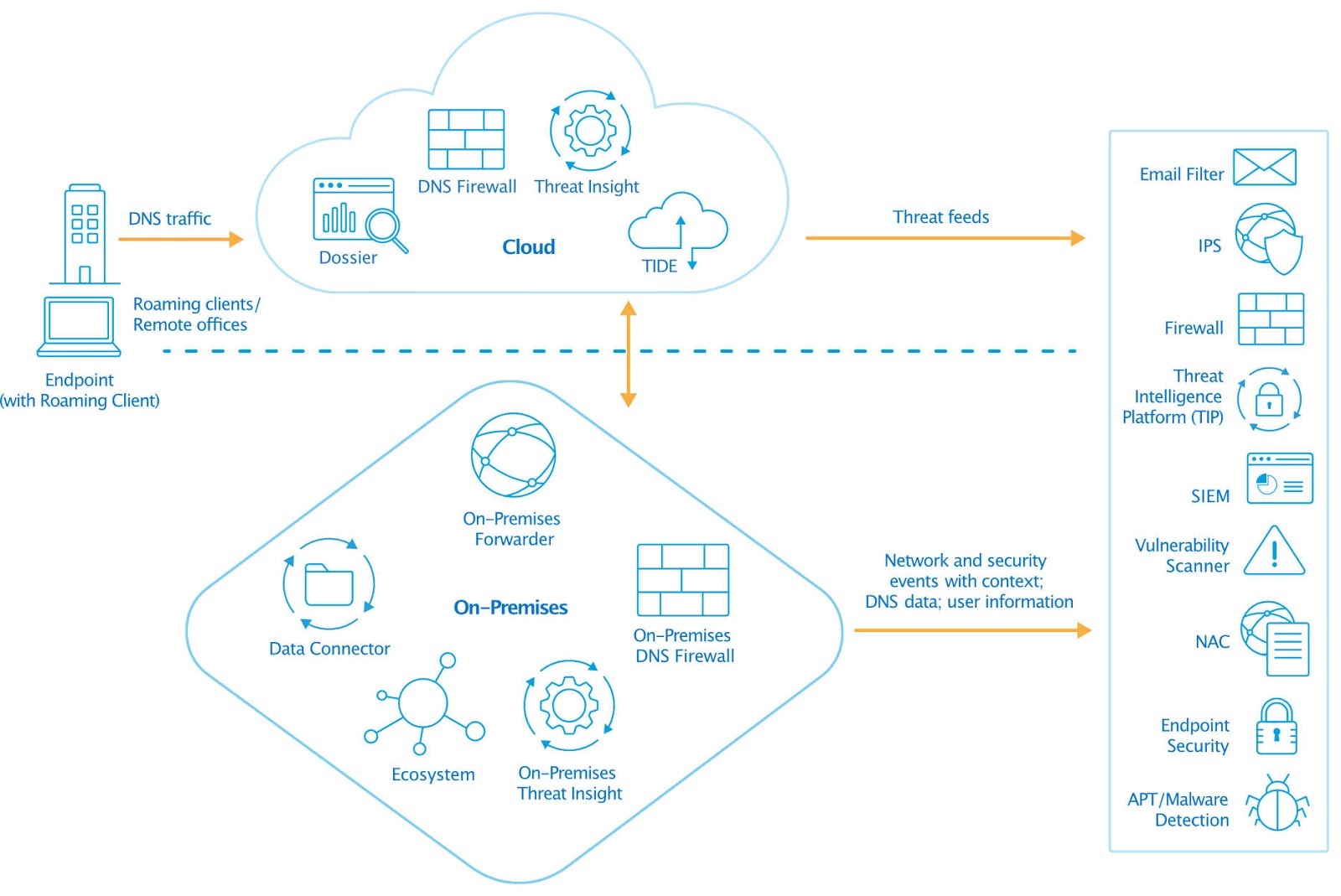
Infoblox BloxOne Threat Defense provides hybrid protective DNS services to secure networks, devices, and users from cyberthreats on and off-premises. The solution analyzes DNS queries to detect and block malware communications, DNS-based data exfiltration, phishing, ransomware, and advanced threats such as DGAs (Domain Generation Algorithms) and lookalike domains. The solution leverages AI/Machine learning algorithms, and threat intelligence feeds to detect known and unknown threats for broader protection. It also helps with faster threat response by integrating with security ecosystem tools such as SIEM, SOAR, ITSM, vulnerability scanners, NAC, and endpoint security using APIs and native out-of-the-box integrations.
Infoblox BloxOne Threat Defense provides the protective DNS services to secure networks, devices, and users.
Learn More about Protective DNS (PDNS) from Infoblox
- BloxOne Threat Defense Advanced – Strengthen and Optimize Your Security Posture from the Foundation (Datasheet)
- Protect Your Network, Brand, and Customers with Custom Lookalike Domain Monitoring (Solution Note)
- Powering Security Orchestration, Automation and Response (SOAR) Solutions from the Foundation
- Threat Intelligence (Solution Note)
- DNS Security Resource Center – Response Policy Zones (RPZ) Overview
[i] Cybersecurity Information: Selecting a Protective DNS Service. US Cybersecurity Requirements Center, March 2021.