SOLUTION NOTE
ROLE OF DNS IN ADDRESSING
AUSTRALIA’S SECURITY OF
CRITICAL INFRASTRUCTURE
(SOCI) ACT
INTRODUCTION
The Australian Security of Critical Infrastructure Act, enacted in 2018, designates certain sectors as critical
infrastructure due to their vital importance to the nation’s economy, security, and societal structure. The
SOCI Act’s designated 11 critical infrastructure sectors are:
- Communications: This includes telecommunications networks, data centers and broadcasting infrastructure (broadcasting, Domain Name Systems (DNS), and telecommunications). Critical Domain Name Systems (defined within the Act) are those managed by entities crucial for administering Australian domain names (.au ccTLD system). These include the registry database, public WHOIS service, .au top-level DNS servers, and specific second-level servers (.com.au, .asn.au, etc.).
- Data Storage and Processing: This covers data centers, cloud services, and more.
- Defense Industry: This includes defense manufacturing, research, and development.
- Energy: This encompasses electricity generation and gas and petroleum infrastructure.
- Financial Services and Markets: This includes banking, insurance, and finance.
- Food and Grocery: This covers food production, processing, distribution, and retail.
- Healthcare and Medical: This includes medical facilities and pharmaceuticals.
- Higher Education and Research: This covers universities and research institutions.
- Space Technology: This involves satellites, ground stations, and more.
- Transport: This includes air, rail, road, and maritime transportation, ports, and airports.
- Water and Sewerage: This covers water treatment, distribution, and waste management.
Australia’s Rising Tide of Cybercrime Created a Compelling Need for SOCI
Australia is grappling with an escalating wave of cybercrime, which includes ransomware, data breaches, and
targeted attacks on critical infrastructure. This includes a significant rise in cybercrime, with data breaches
increasing by 26% in 2023, as reported by the Australian Institute of Criminology. Critical infrastructure
continues to be a prime target, with the ACSC’s 2022-2023 Cyber Threat Report noting a significant increase
in attacks, revealing vulnerabilities within these networks. Ransomware remains a major threat, with several
high-profile attacks causing substantial disruptions and financial losses, including a 2021 attack on a major
logistics company and a 2022 attack on a local government agency.
DNS: YOUR NETWORK’S UNSUNG SECURITY HERO
Imagine your network as a bustling city. DNS acts like the city’s central directory. Every device on the
network, from laptops to printers and even smart thermostats, relies on DNS to find the resources they
need—websites, applications, email servers, and more.
But DNS goes beyond mere directory services. It also holds a wealth of historical and real-time
information. It tracks which users and devices are accessing which resources, offering a complete
picture of network activity.
Here’s why this makes DNS a powerful security tool:
- Universal Visibility: Unlike other security measures, DNS is present at every network touchpoint. It’s the first stop for any device attempting to communicate, making it ideal for monitoring activity across all endpoints—user devices, infrastructure, and cloud environments.
- Early Detection: Traditional security often focuses on user devices. DNS, however, can also watch infrastructure for suspicious behavior. For instance, new DNS requests connecting to malware command-and-control servers could originate from compromised network equipment, not just user machines.
This unique vantage point allows DNS to function as a ubiquitous security control point, safeguarding your
entire network—on-premises, remote, and cloud-based. It’s a familiar tool transformed into a powerful line of
defense, turning everyday operations into a shield against cyber threats.
INFOBLOX: YOUR ALLY IN ACHIEVING SOCI COMPLIANCE
Infoblox provides robust network security and management solutions that empower organizations to meet
SOCI compliance. Here’s how we do it:
| Category | Description |
|---|---|
| Network Design and Architecture | Zero Trust Architecture (ZTA): While not a direct ZTA solution, Infoblox provides foundational elements for ZTA implementation. Infoblox offers granular control over DNS and IPAM, which facilitates the policy-based access controls required for ZTA. |
| Integration with Other Security Solutions: Infoblox’s solutions can integrate with other security technologies, such as firewalls, gateways, vulnerability management, and SIEM solutions, enhancing overall security posture and aiding SOCI Act compliance. | |
| Network Security Controls | DNS Detection and Response: Infoblox’s DNS-level security features protect against threats like ransomware, phishing, botnets, lookalike domains, Zero Day DNS threats, and more. |
| IPAM: Prevents IP address conflicts and unauthorized assignments while providing context for faster incident response. | |
| DHCP Management: Protects against DHCP spoofing and gathers fingerprint data on joining devices for better visibility. | |
| Threat Intelligence: Applies DNS analytics to block high-risk domains before they’re weaponized—supports SOCI risk mitigation. | |
| Network Monitoring and Management | Network Discovery: Provides visibility into network devices to identify vulnerabilities and threats. |
| IPAM: Tracks IP usage, identifies unused IPs, and prevents exhaustion. | |
| DNS Analytics: Offers insights into DNS traffic to detect anomalies and threats. | |
| Automation and Orchestration: Integrates with IT/security tools to reduce manual effort and speed up incident response. | |
| Supply Chain Security | Supply Chain Security: Provides visibility into devices and potential malicious activity to help secure supply chains. |
| Managed Domain Monitoring Service: Monitors supplier domains for lookalikes to prevent vendor trust exploitation. | |
| Risk Management and Incident Response | Risk Management: Tools to identify and manage DNS-related risks supporting SOCI compliance. |
| Incident Response: Provides DNS, user, and device visibility to support investigations. | |
| Compliance Reporting: Supplies data on network activity and control effectiveness to aid SOCI Act reporting. | |
| AI-Powered SOC Insights: Leverages BloxOne Threat Defense to transform DNS and security data into actionable insights. | |
| Infoblox’s Dossier: Investigative tool providing fast, contextual data on domains, IPs, and URLs for security analysts. |
By leveraging Infoblox technology, organizations can significantly enhance their ability to comply with the
SOCI Act’s requirements, particularly in areas related to DNS security, network visibility, and IPAM.
Benefits include:
- 34% Reduction in Security Operations Effort: Infoblox streamlines security processes, freeing up valuable time for security operations center (SOC)/security specialists to focus on critical tasks.
- 47% Reduction in Security-Related Endpoint Downtime: Infoblox keeps devices operational and users productive by minimizing false positives.
- 50% Reduction in Endpoint Detection and Response (EDR) and Firewall (FW) Alerts: Infoblox drastically cuts through the noise, allowing security teams to prioritize genuine threats.
- $400,000 in Annual Productivity Savings: Infoblox’s efficiency translates to significant business cost savings.
CONCLUSION AND RECOMMENDATIONS
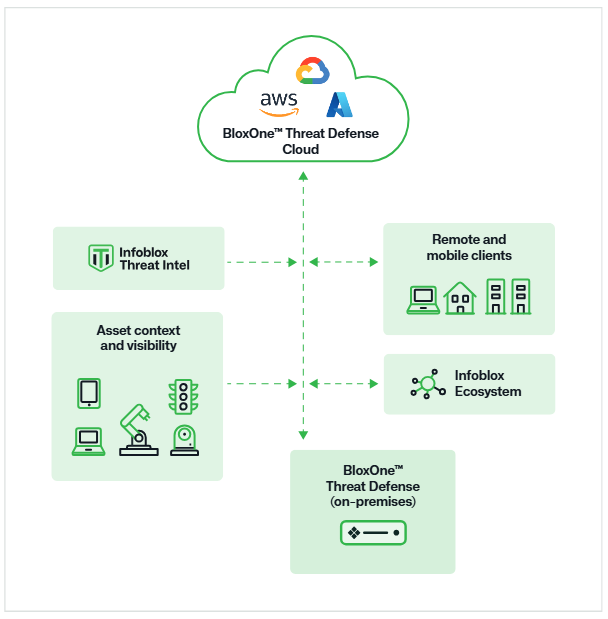
Figure 1: DNS detection and response with BloxOne Threat Defense
Infoblox is an essential cybersecurity partner in your SOCI compliance journey. We aim to unite security and networking teams, empowering businesses to elevate and enhance their security posture. We help organizations turn common, ubiquitous services, such as DDI, into a more powerful capability that provides an integrated, automated defensive shield with proactive offensive threat-hunting capability.
Reach out to us via https://www.infoblox.com/company/contact/